How to protect against BEC & AiTM attacks via Microsoft 365 Defender | Automatic Attack Disruption
The number of BEC (Business Email Compromise) and AiTM (Adversary in The Middle) attacks are growing significantly since 2023 (source: Abnormal security) and are getting more complex (e.g. via the use of the supply chain attacks and manual interaction).

BEC (Business Email Compromise) is a phishing attack used by bad actors for financial gains. The bad actor tries to get access (via credential compromise) to a (example) C-level management mailbox with mandate to send payment request via e-mail(s) to the financial department, internal or external parter organizations (supply chain attack and repeat the process).

The BEC attack performs (high level) the following steps:
- Attackers targets one or more (high level) individual(s)
via OSINT like LinkedIn, Facebook/Instragram, etc. - Send spear (targeted) phishing e-mail to lure the user to a fake logon page (e.g. via a reverse or indirect proxy)
- Credentials are compromised (complex password does not help) and the attackers has access to the mailbox; this can be prevented via MFA or even better contextual MFA (number matching, location and application) to prevent MFA fatique
- Spear phishing email(s) are send from the compromised mailbox to internal and/or to partner organizations with a changed bank account number
- The attacked individual (financial department) sends money to the attacker bank account
- The process repeats itself (supply chain attack)
AiTM (Adversary in The Middle) attacks are kind of the same type of attack, the exception is the account credentials are not (only) compromised but also the session cookie (replay does not require an MFA challenge), for example via EvilGinx. This can be prevented via phish resistant MFA like 1) FIDO2 security keys, 2) Windows Hello for Business or 3) Azure certificate-based authentication.
Azure AD | Conditional Access for Device Compliance
The use of Azure AD | (contextual) MFA and Azure AD | Conditional Access for (hybrid) joined and/or compliant (includes MDE onboarded) devices can also be seen as a phish resistant method because a bad actor cannot access the mailbox with credentials only, also requires a compliant managed device.

A device must be compliant (Microsoft Defender AV Security baseline and Microsoft Defender for Endpoint deployed and healthy) before access is granted to corporate (Office 365) resources via Conditional Access.

Why is Conditional Access for compliant devices (includes MDE as requirement) so important?
- Central log data is only available on MDE deployed devices in case of IR (Incident Response).
- Protection via Microsoft Defender for Endpoint | AV & EDR features is only available on MDE onboarded devices.
- Protection via Microsoft 365 Defender | Automatic Attack Disruption is only available on MDE onboarded devices.
Conditional access for compliant devices prevents unsecure (e.g. home computer) devices to access corporate data.
Microsoft 365 Defender | Automatic Attack Disruption
Automatic Attack Disruption (GA since 23–05–2023) is an XDR (leverage AI) feature (enabled by default) of Microsoft 365 Defender which disrupts a classified attack (e.g. BEC or AiTM) within minutes of (high confidence) detection by isolating the compromised assets.

The feature Classifies the attack (e.g. BEC, Fraud or Compromised User and Mailbox) and Disrupts the attack before it can continue to spread. At the time of writing (08–02–2023), three attack types are supported by Automatic Attack Disruption:
- BEC (Business Email Compromise)
- AiTM (Adversary in The Middle)
- Human Operated Ransomware is an active attack that infiltrate an organization’s on-premises or cloud IT infrastructure, elevate their privileges, and deploy ransomware to critical data.
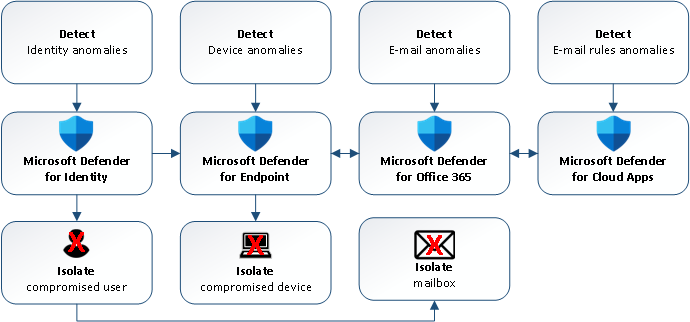
The Detection (alert correlation), Classification and Disruption (containment) is done via Microsoft 365 Defender:
- Azure AD Identity Protection; detects Azure AD sign-in anomalies
- Microsoft Defender for Identity requires the configuration of the Action account for disruption.
- Microsoft Defender for Endpoint; detects anomalies and/or attacks on the device. Requries configuration of Device discovery (set to Standard discovery) and Automation level for Device groups (set to Full) for disruption.

- Microsoft Defender for Office 365 ; detects reading e-mails, sending and/or deletion of e-mails.
- Microsoft Defender for Cloud Apps; detects inbox rule creation.
Pro-tip: excluding one of the products / assets above (e.g. allow the use of BYOD without MDE like home computers) breaks the feature.
Disruption of the attack is done via isolating the compromised asset(s):
- Contain Device; blocks inbound/outbound traffic from MDE onboarded devices with the compromised device via Microsoft Defender for Endpoint

Microsoft Feature Request: Device Isolation (blocks outbound traffic of the compromised device) instead of Device Containment (blocks inbound traffic only on MDE devices from the compromised device) which protect MDE onboarded and ‘can be onboarded’ devices (= devices without MDE).
- Disable User (and revoke the Token); the compromised user/account is disabled in Active Directory (via Microsoft Defender for Identity) and synchronized to Azure AD to disable the Azure AD account and block access to the mailbox.
- Contain e-mail; the inbox rule is removed and the ‘attacker sent e-mail’ is quarantined.
Exclude users is available although I cannot find any reason why you want to disable a user from the feature because the high value targets for BEC/AiTM attacks (C-level management) should be protected as much as possible.
TLDR;
TLDR; Automatic Attack Disruption detects anomalies and/or attack on assets via Microsoft Defender products, classified the type of attack (e.g. BEC, AiTM, etc.) and disrupts the attack by isolating the compromised assets (e.g. disable user or contain device). In the future, Microsoft will support more types of attacks to disrupt.
