Active Directory reconnaissance and Microsoft Defender XDR detections
Updated blog (from 2020) which describes different Active Directory reconnaissance methods (MS-DOS, PowerShell and PowerSploit) to read the Active Directory information (e.g. domain admins).

The Active Directory environment is configured with Microsoft Defender for Identity and Microsoft Defender for Endpoint (both products are part of Microsoft Defender XDR) to detect the reconnaissance methods of the Active Directory from a compromised computer.
C:\> net user Admin Passw0rd /add /domain
C:\> net localgroup administrators Admin /addFor the reconnaissance we will use a (compromised) domain joined computer (W10–01) and a domain user (Admin) with permissions to log on locally to the computer.
Microsoft Defender for Identity
First we need to verify that the Microsoft Defender for Identity sensor(s) are up-and-running.

Audit is not required for Active Directory LDAP (Lightweight Directory Access Protocol) or SAMR (Security Account Manager Remote) detections but Audit is required other type of detections, to verify Audit settings use the new Microsoft Defender for Identity PowerShell module.
Install-Module DefenderForIdentity
Import-Module DefenderForIdentity
Test-MDIConfiguration -Mode LocalMachine -Configuration NTLMAuditing
or
Test-MDIConfiguration -Mode Domain -Configuration AllTest mode
To detect anomalies a baseline has to be established, to bypass the (30-day) learning mode for SAMR detections we can set Defender for Identity in test mode for all detections (Treshold level Low) or one detection (Threshold level Medium).

Test mode is enabled for User and Group reconnaisance (SAMR). LDAP does not require learning.
Method 1 — Net Command
The MS-DOS command Net can be used to perform actions on Active Directory.
Net group “Domain Admins” /domainThe output shows all members of the Domain Admins group

The anomaly ‘User and group membership reconnaisance (SAMR)’ is detected by Microsoft Defender for Identity

The 3 Security Group are Domain Admins, Enterprise Admins and Schema Admins which I used to test detection.
Method 2— Dsquery Command
The MS-DOS command Dsquery and Dsget can be used to query the Active Directory.
C:\> Dsquery group -name "Domain Admins" | dsget group -members Dsquery requires RSAT (Remote Server Administration Tools) installed
The dsquery command is not detected by Microsoft Defender for Identity by default. To detect the dsquery command on (Domain, Enterprise or Schema) Admin groups, we can create a custom query in Microsoft Defender XDR on the asset Identity and use the Devices | Timeline and Advanced Hunting for building the query.
IdentityQueryEvents
| where ActionType contains "LDAP" and QueryTarget contains "Admins"The dsquery command is detected by Microsoft Defender XDR via the custom alert.

Optional the following actions can be added to the custom detection: the device can be isolated and the account can be disabled.
Method 3 — Get-ADGroupMember Command
The PowerShell command Get-ADGroupMember can be used to get Active Directory group memberships.
PS C:\> Get-ADGroupMember -Identity "Domain Admins"Get-ADGroupMember requires RSAT installed
The output shows group membership of the Domain Admins group.

The PowerShell Get-ADGroupMember command is not detected Microsoft Defender for Identity by default. To detect the Get-ADGroupMember command , we can create a custom query in Microsoft Defender XDR on the asset Device and use the Devices | Timeline and Advanced Hunting for building the query.
DeviceEvents
| where AdditionalFields contains "Get-ADGroupMember"The -Identity parameter “domain admins” cannot be specified in the detection but can be seen in the Devices | Timeline section

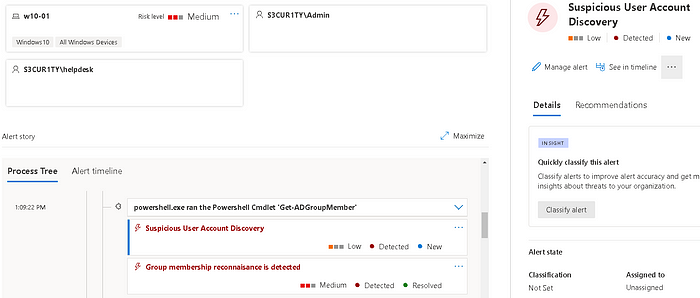
The Get-ADGroupMember command is detected by Microsoft Defender XDR via the custom alert.

And by Microsoft Defender for Endpoint
Method 4— PowerShell Script
The following PowerShell script below does not require the RSAT tools to be installed and query the Active Directory for Domain Admins membership.
$DomainObj = [System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()
$Domain = [ADSI]"LDAP://$DomainObj"
$DN = $Domain.distinguishedName
$DomainAdmins = [ADSI]"LDAP://cn=Domain Admins,cn=Users,$DN"
"Group name " + $DomainAdmins.sAMAccountName
ForEach ($MemberDN In $DomainAdmins.Member)
{
$Member = [ADSI]"LDAP://$MemberDN"
" " + $Member.cn
}The output shows group membership of the Domain Admins group.

The PowerShell script is not detected Microsoft Defender for Identity but is detected by our custom detection User and group membership reconnaisance (LDAP).

And by Microsoft Defender for Endpoint.

Method 5 — PowerSploit
Now let’s use an Active Directory reconnaisance module: PowerSploit | PowerView is a set of functions to perform domain enumeration and exploitation.
Find-LocalAdminAccess
Get-NetUser -SPN | ?{$_.memberof -match 'Domain Admins'}
Get-NetGroup 'Domain Admins'The deployment and usage is detected by Microsoft Defender for Endpoint.

I hope gives some insights and examples of Active Directory reconnaisance but also in the different type of detections from the different products which proves XDR and zero trust in detections is key in detecting different types of attacks.
